DoD Awards Contract To Break Its Security Clearance Logjam
Posted on
Can artificial intelligence, machine learning, and agile development help clear the massive backlog?
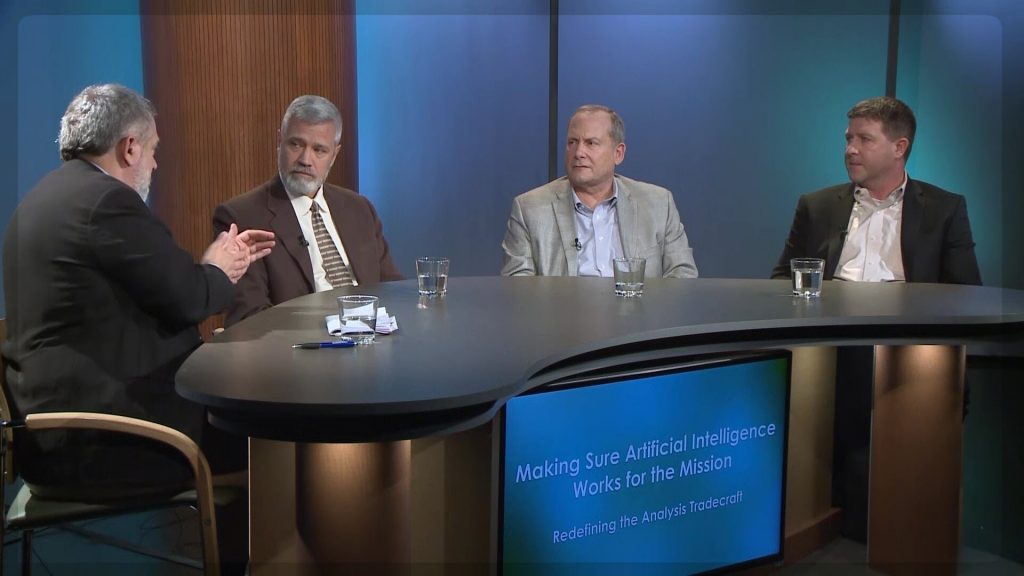
Artificial Intelligence: Ethics, Congress, Data And The Tech [Sponsored]
Posted on
Join me as I explore the intricacies of ethics, technology, policy and politics with three experts on this somewhat arcane subject.
Trump Vs. Huawei: The World Is Watching
Posted on
How the US implements the new Executive Order will have a big impact on whether allies join the American push against Chinese tech.
Army Will Rent Base Networks, But Never Battlefield
Posted on
The Army will effectively rent back-office IT “as a service” from contractors, allowing it to focus on modernizing the front-line network.
End Of Passwords: DISA Tests Walkabout Identity System
Posted on
DISA has identified 46 factors that could be used to help it get rid of passwords on your mobile device, including gait, the way you swipe, and how you hold your phone or tablet.
How To Wage Global Cyber War: Nakasone, Norton, & Deasy
Posted on
The military needs a globe-spanning network to counter threats that no single theater command can cope with. That takes more than just technology.
A ‘Solarium’ For Hacking: Sen. King Launches Cyber Strategy Panel
Posted on
With members from Congress, the executive branch, and the private sector, the commission plans to issue a final report by year’s end.
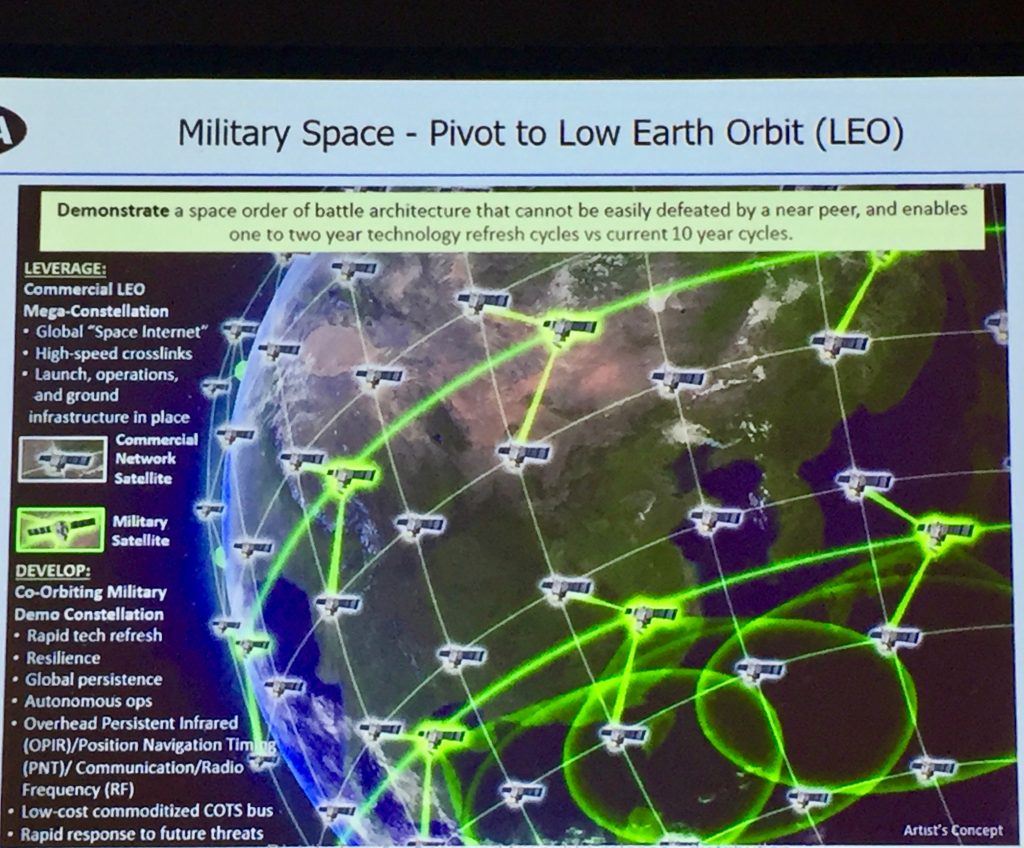
Securing The Space Cloud: It’s Really Hard
Posted on
“Security in space is different than security on Earth,” says Jeb Linton of IBM Watson. “If you lose command and control for even five minutes, your satellite could be completely shut down.”
Can NSA Stop China Copying Its Cyber Weapons?
Posted on
China is copying malware the NSA has used against them. Is this preventable or is it an inherent weakness of cyber warfare?