Securing The Space Cloud: It’s Really Hard
Posted on
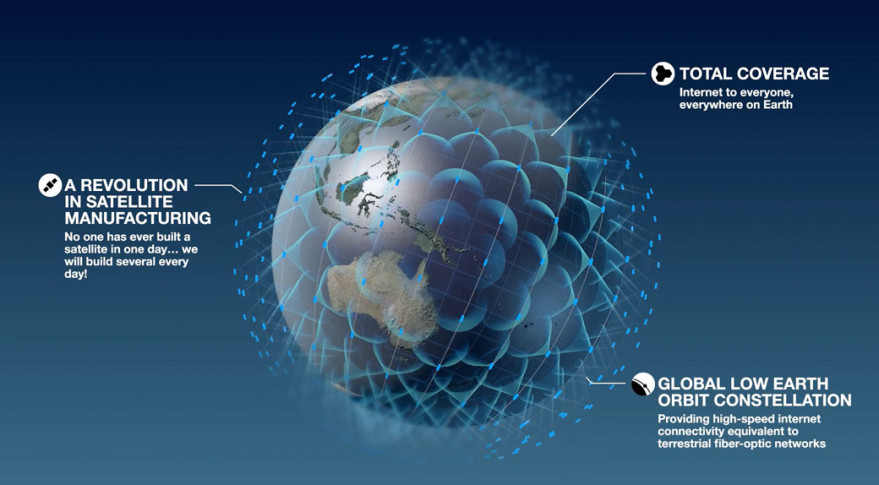
One Web is one of several companies seeking to build a space-based Internet
SATELLITE 2019: If you think it’s hard to secure your systems and data on the ground, think about adding the complications of doing it with satellites forming a space cloud. The answer is going to be complicated, but will rely heavily on resiliency rather than traditional cybersecurity.
Jeb Linton, chief technology officer at IBM Watson & Cloud Platform, said space can make it more difficult than the already highly complex problem DoD faces with network security on the ground. “Security in space is different than security on Earth,” he said. “If you lose command and control for even five minutes, your satellite could be completely shut down,” he explained, and “there is no reset button.”
Satellite constellations will be enabled by cloud-based software and high-speed processors to move vast amounts of data in between each satellite ‘node,’ as well as up and down to land-, sea- and airborne terminals. “The question is how to move all that data without creating a bigger attack surface,” Rusty Thomas, head of the Defense Advanced Research Projects Agency (DARPA) Tactical Technology Office’s Blackjack program, said.
One of the biggest problems, he said, is that “encryption technologies used in terrestrial networks don’t scale well to space.” Indeed, the answer is not “to put big fat encryption on the front end” because “encryption is software that itself is vulnerable, according to Ray Richards, program manager for DARPA’s Information Innovation Office (I2O).
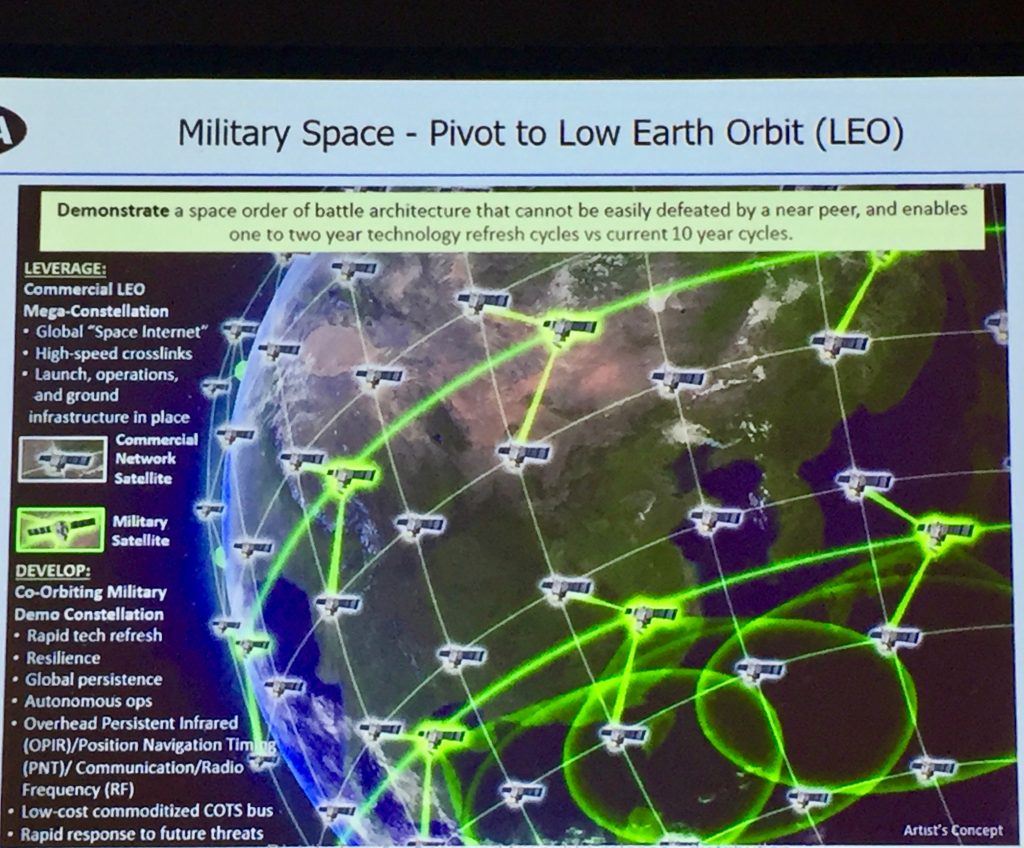
Credit: DARPA
Instead, Richards said, DoD needs to focus on cyber resiliency — and building that resiliency into data networks from the beginning. This is what I2O is trying to do across DoD networks: figure out how to move away from the current model of doing network penetration testing at the end of development and then having to undertake a costly redesign. Instead, the goal is to be able to “evolve software” to create “cyber assurance,” Richards said.
Linton, however, pointed out that the fact that DoD hopes to use commercially available processors in future satellite constellations “opens up the network to hackers.” He suggested that one way to improve the situation would be for DoD create a “white list of software modules” that have been proven secure.
Indeed, DoD hopes to use all sorts of commercially developed technology in future national security satellite constellations, designed to provide resiliency/redundancy to its space architecture currently based on small numbers of large, ‘exquisite’ satellites. Not only that, DoD is eyeing how its space operations could be enhanced by integrating with commercial satellite constellations, such as OneWeb’s planned constellation for providing Internet in space.
DARPA’s Blackjack program is attempting to do both those things. It is aimed at developing an architecture for DoD constellations based in Low Earth Orbit (LEO), using primarily commercially-based technologies — with each DoD-built satellite serving as a “sensor node” that can store and process vast amounts of data on orbit. Under the Blackjack blueprint, the DoD constellation of 90 satellites in 10 orbital planes would further be connected to commercial satellite networks to “leverage the Internet in space.” The network will use cloud software and edge computing, which involve distributed processors and data storage placed closer to the location where data is needed. The heart of the architecture, according to Thomas, will be the C2 system called “Pit Boss” to move data rapidly and securely.
The answer to the complicated cybersecurity problems that this architecture will face, Thomas told me after the panel discussion, may end up being similar to what software use developers use today: patches. “We can have patches for hardware, and patches for software,” he told me. This is because the goal is to create constellations made up of satellites carrying payloads on “commoditized busses” that are designed to be regularly replaced in orbit, using rapid launch capabilities. Further, the “cloud software” carried on each satellite will be designed so that it can be constantly upgraded from the ground as vulnerabilities are found. Thus, Thomas said, the network can be kept up ahead of “the enemy’s ability to find a way to attack.”
The concept of patches for satellite constellations may sound less than ideal to all of us who have struggled with iOS upgrades on our iPhones, or were caught up in the 2017 hack of US credit-reporting bureaus. But Thomas explained that the nature of constellations inherently helps to improve network security, because if you lose one or two “nodes” — that is individual satellites — it’s not such a big deal.
In other words, distributed satellite architectures protect themselves in some ways. And if the goal is resiliency of the the network, rather than cybersecurity for each node, much will rely on the capacity for rapid reconstitution of functionality. This is not an unprecedented approach — many cybersecurity experts make the argument that because cybersecurity will never be 100 percent for any computer network, network resiliency is really the only answer. It’s just a lot harder to achieve when you’re in orbit.
Subscribe to our newsletter
Promotions, new products and sales. Directly to your inbox.
