Fail Fast, Not Twice: DoD’s Push For Agile Software Development
Posted on

Cloud computing servers
WASHINGTON: The Pentagon is pushing hard toward a new software development model that gets the bugs out early through constant testing and improvement, avoiding traditional IT disasters where flaws only become obvious too late. The idea, Air Force Chief Software Officer Nicolas Chaillan said, is “fail fast, but don’t fail twice for the same thing.”

Nicholas Chaillan
Chaillan is co-director of an organization called the DoD Enterprise DevSecOps Initiative. That string of buzzwords translates into English as a campaign to spread the new approach — called DevSecOps because it combines software development, cyber security, and software operations side-by-side — across the entire Department of Defense (i.e. the DoD Enterprise).
Currently the initiative is reviewing more than 100 different development tools and services for potential use across the Department, Chaillan told an AFCEA DC conference last week. It’s also developing metrics and standards, working with Defense Acquisition University to develop a curriculum to teach the DevSecOps methodology, and creating new contracting language to make it easier to use the new approach.
So what is DevSecOps? You have to start by contrasting it to traditional software development process known as “waterfall,” in which work flows in a clear linear sequence from one stage to the next, with no way to flow back upstream to an earlier stage. The waterfall approach still works if you have a very clear idea of what the final product needs to be and that idea won’t change over time — but modern threats moves too fast. As a result, Chaillan said, development takes so long that mission needs change before the software is delivered; coding flaws often aren’t found until the end of the development cycle–sometimes a year of more later–resulting in costly fixes; and cybersecurity is treated as a separate step instead of infused throughout all stages of the development, leading to software vulnerabilities and ineffective bolt-on solutions at the end.
Development Operations or DevOps, by contrast, is what’s known as an “agile” methodology because it embraces an iterative process: develop a little, get user feedback, field a little more, and repeat. Rather than have developers labor in isolation to develop something that looks complete, only for the operators to finally see it and find flaws, DevSecOps races to produce a “minimally viable product” early on that the user can actually try out and give feedback on. The developers can then take that feedback, make improvements, and roll out the next version — improved but still imperfect — for another round of operator feedback.
When you add cybersecurity experts to this process, working alongside both the developers and the users/operators from the beginning to ensure the code isn’t easily hacked, DevOps becomes DevSecOps.
That methodology makes DevSecOps especially useful in developing software that can resist evolving cyber threats from hackers, rogue countries like North Korea, and nation states like Russia. It’s what organizations like the Air Force’s Kessel Run project in Boston are already doing, albeit on a relatively small scale.
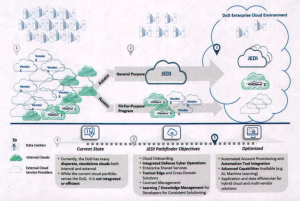
The Defense Department’s strategy to transition to cloud computing. Note the prominent role for the JEDI project. (Click to expand)
Operating on a larger scale for more complex software needs is a joint enterprise-wide DoD effort managed by the Office of the Under Secretary of Defense for Acquisition and Sustainment, the DoD CIO office, and the armed services. The DoD Enterprise DevSecOps Initiative so far has 29 organizations working with it, including Special Operations Command, Transportation Command, Naval Air Systems Command, and the Naval Information Warfare Systems Command (formerly known as SPAWAR).
Chaillan extolled a variety of benefits of agile software development. It will permit every DoD organization to “deploy a hardened software factory on their existing or new environments, including classified, disconnected and clouds, within days instead of a year, (while providing) tremendous cost and time savings,” he said. Those benefits can be realized with traditional business-process IT, military-unique command, control, and intelligence systems, or even weapons systems.
Other benefits and features that Chaillan touted:
- bug and security fixes in minutes instead of weeks or months;
- continuous feedback from the warfighters that need and use the software, instead of a rigid separation between developer and end-user;
- automated testing and security, instead of laborious and fallible manual checking of countless lines of code;
- a Continuous Authorization to Operate (ATO) process for rapid deployment and scalability, instead of having to develop a final product and then wait for a lengthy security review before actually using it;
- holistic and “baked-in” cybersecurity instead of constantly scrambling to patch problems after the fact;
- use of “microservices,” discrete, modular capabilities that can be quickly added to existing software, instead of having to reinvent the wheel and develop such functions anew for each project; and
- the ability to deploy the same software on any environment, including DoD-approved cloud services.
Subscribe to our newsletter
Promotions, new products and sales. Directly to your inbox.
