Unsafe At Any Speed: Multiple Vulnerabilities Afflict 5G
Posted on
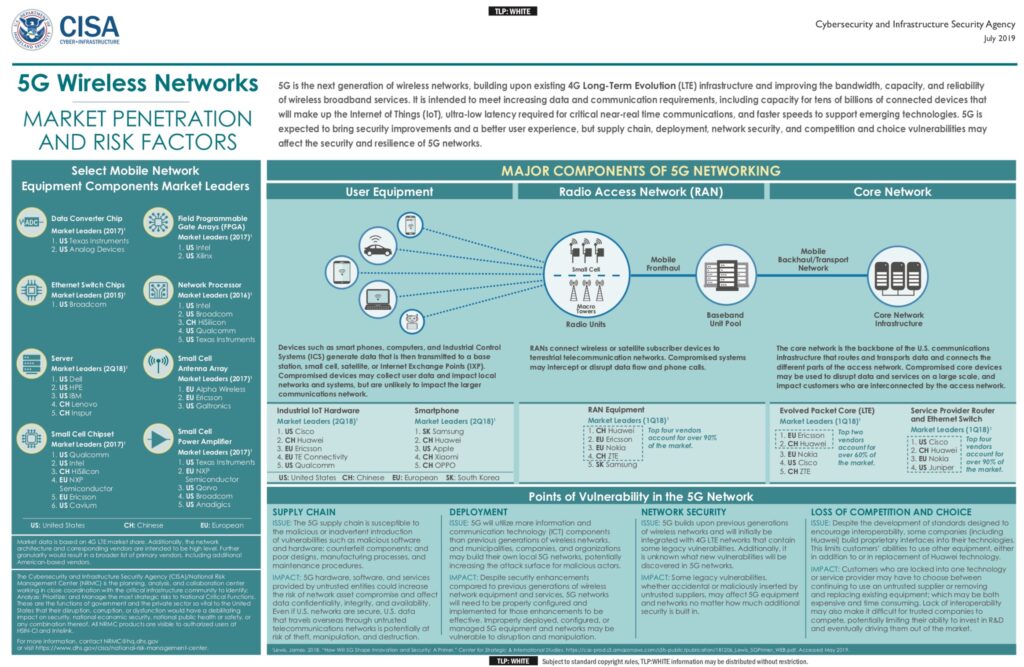
US government agencies, especially the military, need to be wary of embracing 5G network technology, despite its benefits, simply because so many vendors are based in China. That means military networks may lag behind capabilities widely available to ordinary citizens with the latest smartphones.
“Use of 5G components manufactured by untrusted companies could expose U.S. entities to risks introduced by malicious software and hardware, counterfeit components, and component flaws caused by poor manufacturing processes and maintenance procedures,” concludes the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), which recently released a 16-page overview of the security risks introduced by 5G adoption in the U.S.
“5G hardware, software, and services provided by untrusted entities could increase the risk of compromise to the confidentiality, integrity, and availability of network assets,” the report says. “Even if U.S. networks are secure, U.S. data that travels overseas through untrusted telecommunication networks is potentially at risk of interception, manipulation, disruption, and destruction.”
Present-day 4G Long-Term Evolution (LTE) networks have throughput in the 100 megabits per second (Mbps) range and a latency of under 100 milliseconds. 5G is expected to increase data rates to 20 gigabytes per second (Gbps) — that’s a 1,600-fold increase — and reduce latency 95 percent, to under 5 milliseconds. Such lightning-fast connections are seen as essential to a host of new applications, like self-driving cars and linking of billions of ordinary appliances into a sprawling Internet of Things.
But along with those benefits, however, come a truckload of security vulnerabilities that fall into four categories: the supply chain could include bugged or sabotaged hardware and software; deploying the larger number of smaller systems required for 5G could create new openings for attack; network security could suffer as new 5G systems are layered on top of existing 4G ones; and competition and choice could erode in the face of rising global giants like Huawei.
“There remain the same security vulnerabilities that exist today in all wireless networks: hardware, software, data model, power application, supply chain,” said retired Air Force Brig. Gen. Robert Spalding, former chief China strategist for the chairman of the Joint Chiefs of Staff and the Joint Staff, and former senior director for strategic planning at the White House National Security Council.
“The main difference is the enhanced speed and connectivity. More bandwidth and lower latency will mean an exponential increase in the threat landscape. Total connections will move from 10,000 to 3 million per square mile. These extra connections will be machines that track everything we do,” Spalding told me. “These vulnerabilities would make 5G unusable for the military, unless mitigated.”
While at the National Security Council, Spalding gained notoriety for a leaked memo in early 2018 where he advocated on security grounds for a nationalized American 5G network. He is presently a senior fellow at the conservative Hudson Institute.
Following are details about the four areas of 5G vulnerability identified by DHS CISA:
Supply Chain: Use of 5G components manufactured by untrusted companies raise the threat of malicious software and hardware, counterfeit components, and poorly designed and manufactured systems that will be vulnerable to cyberattack and disruption.
- “Compromised devices may provide malicious actors with persistent access to 5G networks and the capability to intercept data that routes through the devices,” states the overview report. “Compromised devices may infect connected computers, phones, and other devices with malware and may have data rerouted, changed, or deleted. Untrusted companies that have significant international market share within telecommunication networks may introduce risks even if they do not have a large presence within the U.S networks. Therefore, even if the U.S. network were completely secure, data traveling overseas may pass through untrusted telecommunication networks and potentially be vulnerable to interception, manipulation, disruption, or destruction.”
Network Security: As 5G will be built atop existing 4G infrastructure, who knows what vulnerabilities will continue to unfold in 4G as it is bolted onto forthcoming 5G equipment, and what new dangers 5G will reveal?
- “5G technologies will initially be overlaid on the existing 4G Long-Term Evolution (LTE) network that contains legacy vulnerabilities. These could be inadvertent, technical vulnerabilities inherent to the network, or due to 5G technologies’ integration into untrusted 4G and 4G LTE networks. The inheritance of security settings, permissions, and technical specifications from an untrusted core network may negate built-in 5G device security.”
Network Deployment: 5G means a bigger infrastructure, which means more targets for interception, manipulation, disruption, and destruction.
- “Infrastructure will likely include, but is not limited to cellular towers, beamforming, small cells, and mobile devices. Unlike traditional cellular towers, small cells will be densely deployed in metropolitan areas, residing on light poles, trees, homes, building corners, and retail shops. Although small cells are designed with physical security features, they still could be compromised through physical access. This may provide malicious actors with persistent illicit access to the 5G network, the ability to intercept data routed through the device, and an avenue to conduct Denial of Service attacks on devices communicating with that small cell.”
Loss of Competition and Trusted Options: Here the report calls out untrusted companies like China’s Huawei and ZTE for not supporting standards and building proprietary interfaces into their products.
- “Although limited in their share of the U.S. telecommunications market, these companies have significant market share internationally and may be less likely to participate in interoperability efforts. Communication network operators that previously purchased 4G equipment from a company like Huawei that uses proprietary interfaces in their technologies cannot easily use other vendors’ equipment for 5G, which could negatively affect competitive balance within the 5G market. Loss of market share could limit trusted companies’ ability to invest in research and development and could eventually drive them out of the market. Loss of trusted suppliers could potentially lead to a situation where untrusted entities are the only options.”
Subscribe to our newsletter
Promotions, new products and sales. Directly to your inbox.
