Navy Issues New Cybersecurity Standards – With More To Come
Posted on

Navy cyber operators
The Navy has issued new cybersecurity standards that every unit, office, and contractor had better get to know. Governing everything from business systems to weapons systems to machinery controls, the standards will govern future information technology acquisitions and provide a benchmark for assessing where existing systems fall short.
The Navy’s just getting started, too. Last week, the Space and Naval Warfare Systems Command published eight standards for such things as “network firewalls” and “vulnerability scanning.” But those are just the eight most urgent, said SPAWAR’s commander, Rear Adm. David Lewis.

Rear Adm. David Lewis
Ultimately, “we envision about 38 standards to be published by the Navy… between now and ’18,” Lewis told me. “The endstate is those 38 standards [containing] about 970 controls, [each] a sentence or a paragraph that says ‘you’ll do this.'”
The 38 standards and 970 controls apply to the entire Navy network as a whole, not to every single system, component, or piece of hardware purchased, Lewis emphasized. A very different subset of standards will apply to, say, a network gateway to the Internet than to an embedded processor on a weapons system.
“Depending on where a system is in the overall big Navy architecture, certain standards will be more applicable,” he said. Further, he said, “we don’t necessarily always have to follow them.” For a notional example, if 100 controls apply to a particular function, but the only vendor that meets all 100 charges an unaffordable amount, the Navy will have freedom to buy another vendor’s 50 percent solution for a tenth the price.
The standards aren’t supposed to be a straitjacket, in other words, but a measuring stick. The Navy will still make made tradeoffs of cost, benefit, and risk, but now, said “we have a objective way of assessing what the risks are” Lewis said, “[so] we as the buyer can make risk-based assessments of what we’re getting.” That gets away from the “subjective assessment… which tends to dominate our conversations today.”
“With each system, we look at the standards that apply to that system; we assess its performance against the controls; and now we have an objective measure,” Lewis continued. By highlighting areas of vulnerability, he said, “it helps target our modernization, it helps target our future contracts.”
That applies just not to new systems but to upgrading existing ones. “We can take the standards and use it as a measuring tool against the systems that are already out there,” he said. “We can grade ourselves against that and say, ‘hey, we got 80 out of 100 already. So when we look to modernize in the future, we should focus on the other 20.'”
So what are the standards like, in layman’s terms? While promulgated by SPAWAR, they’re the product of consultation among all the Navy’s major systems commands, represented on something called the Information Technology / Information Assurance Technical Authority Board. They’re also based on civilian standards developed by NIST, the National Institute of Standards and Technology.
“We went through the NIST standards and modified them where we felt they needed to be modified to make them more specific and more relevant to Navy needs,” Lewis said. “We kept most of what was in NIST.” Unlike the NIST standards, however, the full Navy standards will not be public, being available instead only to “U.S. government organizations and authorized industry companies.”
The underlying philosophy is breaking what some experts call the “cyber kill chain,” though Lewis prefers “detect to engage sequence.” That’s the necessary sequence of steps a hacker must complete in order to succeed, from first scouting out the target to getting inside it to extracting data or sabotaging software. An Internet gateway needs to be focused on stopping the first steps of the chain, while an embedded system deep within the Navy network will only encounter an enemy who’s already gotten in.
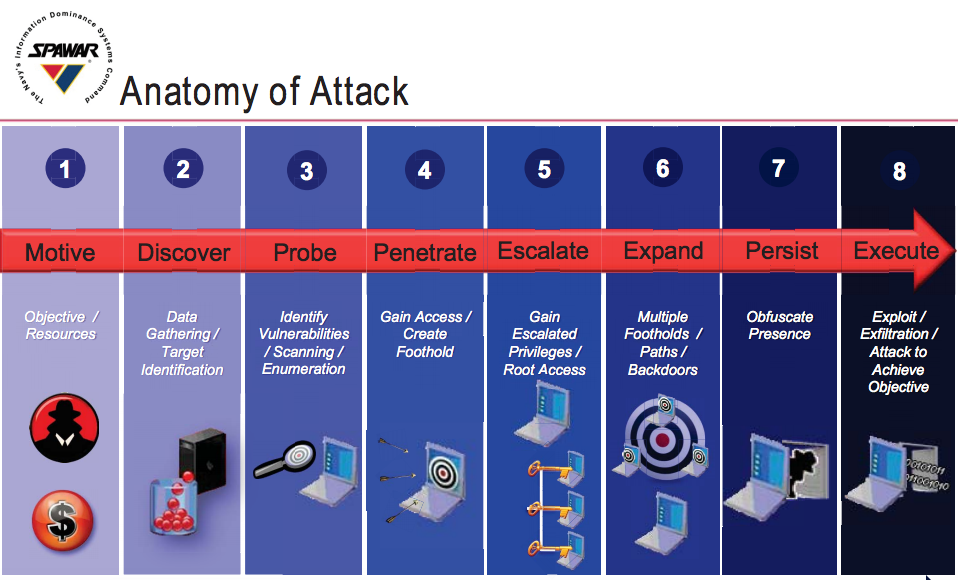
A Navy depiction of the “cyber kill chain”
In the Navy, “we have a very good perimeter defense structure in place already,” Lewis said. “Inside a tactical system on a ship, I’m pretty far away from that [perimeter]. What I’m more interested in is maybe step four or five, where someone is in the system and trying to maneuver internally… how to detect somebody who’s in my network… what are the tools I might need to find them… to isolate them and to shut them down.”
Some of the standards specifically require a “defense in depth” approach: Rather than traditional firewalls, which try to keep any intruder from getting in, the new standards assume some intruders may get in and compartmentalize the system, so a hacker who gets access to Section A can’t then easily infect Sections B, C, and D.
“The key to that is defining interfaces between systems and collections of systems called enclaves,” said Lewis. “That actually works hand in glove with open architecture,” the philosophy of building information technology in plug-and-play modules. If the architecture isolates each component of the system so they can be easily replaced — the goal of open architecture — then it can also isolate them so they can’t easily infect each other — the goal of defense in depth.
The first eight standards specifically cover “Host Level Protection; Network Firewall; Network Intrusion Detection Systems and Intrusion Protection Systems; Defense in Depth Functional Implementation Architecture; Security Information and Event Management Implementation; Information Security Continuous Monitoring; Boundary Protection; [and] Vulnerability Scanning.”
“This is really fundamental stuff to get through our cybersecurity issues in a coherent and objective manner,” Lewis told me.
Subscribe to our newsletter
Promotions, new products and sales. Directly to your inbox.
