Know Your Enemy: Lockheed Touts ‘Intelligence-Driven’ Cybersecurity
Posted on
If you know the enemy and know yourself, you need not fear the outcome of one hundred battles — Sun Tzu
ROCKVILLE, MD: In a bland office building 30 minutes from the Pentagon, a wall-mounted screen shows, in real time, every suspicious email and LinkedIn request sent to employees of Lockheed Martin, the world’s largest defense contractor. With 98,000 people worldwide working on some 8,500 programs, the company’s network interacts with the internet 20 billion times a day. That’s more than 230,00 events per second.
99 percent of those events — emails, pings, logs, etcetera ad nauseam — are “mostly meaningless,” Lockheed’s cyber intelligence director, Mike Gordon, told me and a fellow journalist this morning. But buried in that gigantic haystack are a handful of poison-tipped needles.
Russia, China, North Korea, and other advanced adversaries want intelligence on the US and allied weapons that Lockheed Martin makes, from the F-35 fighter and the Littoral Combat Ship to hypersonic missiles and missile defenses. Such nation-state actors have been attacking Lockheed since at least 2003, Gordon and his colleagues said. How can the company know which events out of billions require it to take action?
It’s widely known in cybersecurity circles that you can’t rely on antivirus and firewalls, since those work by matching incoming traffic against databases of known malware. Sophisticated adversaries constantly change their tactics, so there’s no fixed “signature” to detect. But you can’t rely on so-called anomaly detection to warn you of an intruder in your system, either, since by the time you’re seeing weird activity on your network, the attackers are already inside. Instead, Lockheed protects itself — and its paying clients — by looking for the characteristic behaviors of particular attackers, a strategy it calls “intelligence-driven defense.”
Intelligence-Driven Defense
Lockheed estimates the truly dangerous actors — known as Advanced Persistent Threats (APTs) — collectively try hundreds of distinct attack techniques on the company every year. Each of those attack campaigns may potentially involve hundreds of individual emails, pings, or other detectable events.
The techniques used change over time. One trend noticeable over the years, as Lockheed itself has become better-defended, is increasing attacks on its 16,000 suppliers and contractors, seeking an indirect route to the prime contractor and the government itself. There are legal limits on discussing contracts with third parties, and subcontractors often dislike disclosing who their sub-sub-contractors are, lest the prime contractor decide to cut out the middleman. But Lockheed and the Pentagon are working to add clauses to contracts that would give the government, if not Lockheed, full visibility into every part of the supply chain.
Another trend is increasing use of social media, notably Facebook and LinkedIn, to gather detailed intelligence about Lockheed and subcontractor employees and then develop exquisitely custom-tailored attacks. Gordon said some hackers pose as recruiters, copying real job postings off the internet, and send their targets several innocuous emails to establish rapport before springing the trap with malicious code hidden in a link labeled “click to upload your resume” or even in a PDF map of where to meet for an interview.
But those trends will change. A smart adversary won’t keep attacking the same weak points with the same malware from the same IP address over and over and over, Gordon and his colleagues explained. That said, the bad guys can’t afford the time and money to reinvent the wheel every time they attack. That means you can find some recurring patterns that let you build a profile of a particular attacker, which in turn lets you discover attacks you might have missed.
Discovering more attacks, in turn, lets you accumulate more clues to build a better profile to discover more attacks to accumulate more clues. The goal of intelligence-driven defense is a positive feedback loop. That’s much like its namesake, intelligence-driven operations in counterterrorism, where special operators grab a target, so intelligence analysts can ransack his cellphone to find his associates, so the operators can grab them and their phones in turn.
The framework Lockheed uses for this intelligence-gathering is what it calls the Cyber Kill Chain®. (Yes, Lockheed managed to register that as a trademark, even though it’s simply sticking two generic terms together). “Kill chain” is military jargon for all the steps you need to take to perform a mission, from gathering reconnaissance to launching a weapon to assessing the damage. All these activities have to take place in cyberspace too — they’re just intangible — and at each step, the attacker leaves clues the defender can detect and performs tasks the defender can disrupt.
Lockheed identifies seven distinct steps in the kill chain for a successful attack, from reconnaissance to exploitation to final “actions on objectives” such as copying secret data. While smart adversaries will probably change their techniques for one or more of these steps, the odds are low they’ll change all seven every time. That means at least some of the telltales of past attacks — an IP address, a scrap of code — will show up in future ones, allowing you to catch them before they’re complete, preferably so early they’re still scanning your system for weak points.
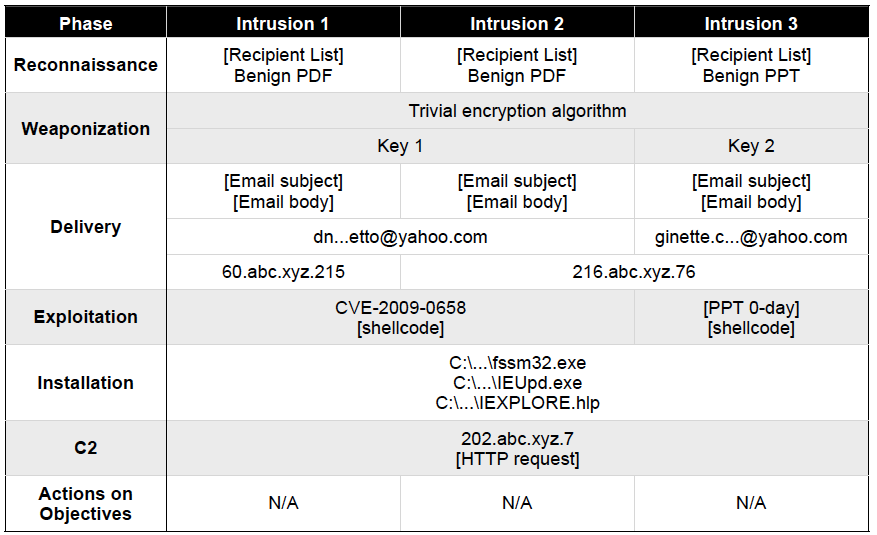
Advanced hackers will change some of their techniques from one attack to the next, but not all, allowing cybersecurity analysts to use telltales from one intrusion to help them find the next. (Lockheed Martin graphic)
Big Data, AI, & Humans
Finding these recurring patterns requires analyzing large amounts of data, the more the better. Lockheed’s sheer size means it collects and at least temporarily stores a petabyte a day: For reference, that’s enough to fill the laptop I’m writing this on and 125,000 others like it.
To deal with these masses of data, Lockheed is investing heavily in big data analytics, artificial intelligence, and machine learning. The goal is to let a set of algorithms monitor a network or weapons system long enough to teach itself the patterns of normal operation. Then it can alert human operators to the abnormal.
For now, cybersecurity still depends on human minds, Gordon and his colleagues said. Lockheed’s actually reorganized its global operations so someone’s always awake and watching, but no one’s slogging heavy-lidded through a graveyard shift: They now have overlapping shifts run both by large teams in Rockville and Denver and four-man cells in Britain and Australia. The larger centers include not just analysts but in-house coders to write new tools as needed, reverse-engineering specialists to take apart the attacking code, and infrastructure experts who help run Lockheed’s vast networks, all sitting side by side to ease collaboration.
Those talented humans are in high demand, said Doug Booth, the business development director who markets Lockheed’s cybersecurity tools, services, and training — much of it developed initially for the company’s self-defense — to outside clients like the Pentagon and allied nations. “We have hundreds of openings” in his part of Lockheed alone, Booth said, thousands across the company as a whole.
“We talk about all the tools and technologies,” Booth said, “(but) really the most valuable asset in this cyber fight is a trained warrior.”
Subscribe to our newsletter
Promotions, new products and sales. Directly to your inbox.