DISA Launches 5 Cloud Tests, Warns On Industry Consolidation
Posted on
FORT MEADE, MD: “Remember the peace dividend we took in the Clinton years in the ’90s? Welcome back,” said Douglas Packard. “That’s where we’re at.”
Some 20 years ago as defense budgets plummeted post-Cold War, the defense industry consolidated, recalled Packard, acting head of procurement at the Defense Information Systems Agency. Contractors better beware once more, because budgets are tightening again: “the Department [of Defense] will, we believe, be sequestered in ’16,” he told reporters yesterday. (Note that Sen. Carl Levin, outgoing chair of the Senate Armed Services Committee, yesterday made much more hopeful noises about forestalling sequestration, a series of automatic spending cuts required by current law).
So DISA, which this fiscal year will buy over $8 billion in cyber and IT products and services for the rest of the Defense Department, is looking for every opportunity to save in 2015 and beyond. That includes relentlessly competing contracts wherever possible, rather than using single-source contracts that are currently all too common. It also includes systematically consolidating contracts where multiple firms are currently providing a similar product or service, where multiple military organizations are independently buying similar things, or where individual bases and commands have one-off arrangements that could be consolidated into a wider regional contract.
DISA is also consolidating internally. “We have over a hundred service desks scattered across the globe” dealing with different DISA products and customers, said agency CIO David Bennett, addressing contractors at yesterday’s annual Forecast To Industry here on Fort Meade. “[We] will consolidate that into one service desk for the agency… into one conceptual, virtual service desk that will support the agency products worldwide.”

DISA director Lt. Gen. Ronnie Hawkins addresses contractors at the agency’s 2014 Forecast To Industry.
DISA’s ultimate goal is to centralize Defense Department computing as much as possible into 10 Core Data Centers (CDCs): eight in the continental United States, one in Germany (actually a “virtual” center combining two physical locations), and one at a location to be determined in the Pacific Command theater. DISA believes this “virtualized infrastructure” will be more effective, cheaper to operate, and easier to defend from hackers than current patchwork, in which most Defense Department organizations have their own network equipment physically on-site.
Already, Bennett said, the Defense Manpower Data Center (DMDC) and Defense Logistics Agency (DLA) are moving more and more of their operations from their in-house data centers — which will soon shut down — to DISA’s Core Data Centers. The Army also has a “very aggressive” plan to move operations to the CDCs, he said. (The Navy Department, by contrast, often seems aloof to DISA initiatives).
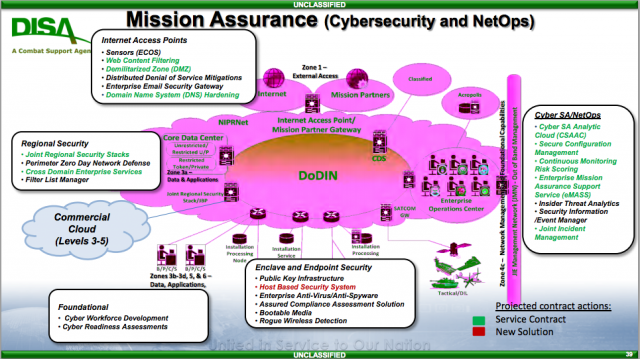
DISA is still struggling to incorporate commercial cloud services (lower left) into the Department of Defense Information Networks (DoDIN).
A Cloudy Future
Standing somewhat uneasily to one side of this centralized system is the “commercial cloud.” Congress has been pushing federal agencies to use commercially available cloud computing, including a mandate in the 2012 National Defense Authorization Act, but DISA officials admit the agency is still struggling to figure out just how. While the military can hardly outsource command and control of (for example) nuclear weapons, it also has to manage huge amounts of unclassified but still-sensitive information, from contractors’ proposals to troops’ health records. How much protection does this data need? And how can the Pentagon get this protection without expensively reinventing the wheel of what’s already available from, say, Amazon or Google?
DISA’s track record on cloud computing is distinctly mixed. Last year, it opened the door to commercial vendors — but only a crack. In addition to the government-wide FedRAMP (Federal Risk and Authorization Management Program) standards, DISA imposed military-specific security requirements. Only four commercial providers have qualified to handle publicly releasable information (in Pentagonese, Impact Level 1 and 2 data) and only one to handle sensitive-but-unclassified (levels 3, 4, and 5). Which one? DISA declined to say on Wednesday, but Amazon announced yesterday that its Amazon Web Services “has achieved the first DoD Provisional Authorization under the DoD Cloud Security Model’s at security impact levels 3-5. Amazon had already qualified for the lesser security levels. BD readers will remember that Amazon has provided the intelligence community with cloud services for some time.
“We’ve made it too hard,” DISA information assurance chief Mark Orndorff told reporters. While some of DISA’s security concerns proved sufficiently compelling that the rest of the federal government incorporated them into the FedRAMP standards itself, others were just too stringent, he said. DISA is now “doing a detailed scrub” of every requirement that exceeds the (revised) FedRAMP standard and “working on an English-language translation” of its requirements, which Orndorff admits were intelligible to security specialists like himself but impenetrable to almost everyone else in government and industry alike.
One complication is that DISA has tried to compete with commercial cloud services as well as to offer access to them. “Two years ago,” said Bennett, “we dabbled in ‘platform as a service,'” a form of cloud computing that proved too hard to customize to other defense agencies’ needs: “I shut it down.”
This March, DISA rolled out milCloud, an “infrastructure as a service” approach that demands less of the agency. (Under “platform as a service,” DISA provided software development tools to its customers; “infrastructure as a service” just provides customers somewhere to run their own software). But milCloud is controversial. Critics say that DISA invested money and prestige to compete with proven commercial products: That’s not just a sunk cost, it’s an enduring incentive for DISA to steer its military customers away from commercial cloud services and towards milCloud. “For DISA to be both the broker and the provider creates a conflict of interest,” said one industry source.
By contrast, both the Central Intelligence Agency and the Navy have moved public data to Amazon Web Services — and the Navy CIO behind that move, Terry Halvorsen, is now acting CIO of the entire Defense Department. Halvorsen is “personally interested” in driving DISA to open up, Orndorff said.
As a result, “in the next several weeks,” DISA is working with the services to launch five pilot projects in the use of commercial cloud services, one of them in Ordnorff’s own office. While DISA didn’t give many details, Orndorff did say each pilot would include simulated threats to test the ability to detect and react. The lessons learned from those experiments, he said, will guide DISA as it changes its cybersecurity requirements.
Edited 12:15 pm
Subscribe to our newsletter
Promotions, new products and sales. Directly to your inbox.

