Army scientists scout energy solutions for the battlefield
Posted on
DefenceTalk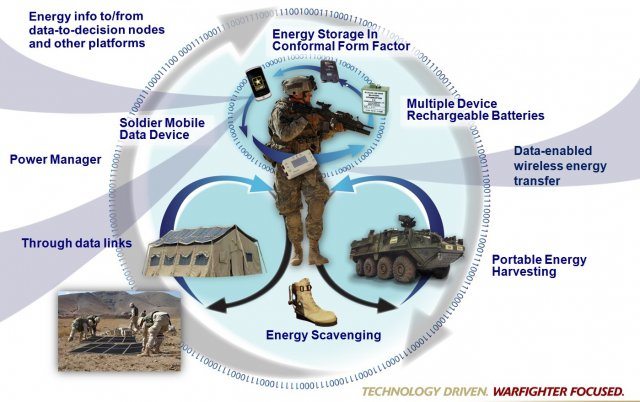 What if scientists and engineers could scavenge energy for warfighters, like bottom feeders scavenge in the ocean? The U.S. Army Research Laboratory, or ARL, along with the Army science and technology community, is pursuing novel technology aspects of the Army’s Operational Energy Strategy. Energy Scavenging is just one way ARL experts are getting more from […]https://www.defencetalk.com/army-scientists-scout-energy-solutions-for-the-battlefield-47590/
What if scientists and engineers could scavenge energy for warfighters, like bottom feeders scavenge in the ocean? The U.S. Army Research Laboratory, or ARL, along with the Army science and technology community, is pursuing novel technology aspects of the Army’s Operational Energy Strategy. Energy Scavenging is just one way ARL experts are getting more from […]https://www.defencetalk.com/army-scientists-scout-energy-solutions-for-the-battlefield-47590/
Tactical Targeting Network Technology for Deck Handling Trials of X-47B
Posted on
DefenceTalk Rockwell Collins Tactical Targeting Network Technology (TTNT) was used by Northrop Grumman Corporation and the U.S. Navy as they successfully completed a series of deck handling trials of the X-47B Unmanned Combat Air System aboard the aircraft carrier USS Harry S. Truman (CVN-75). The exercises demonstrated the ability to maneuver the tailless, strike-fighter-sized aircraft quickly […]https://www.defencetalk.com/tactical-targeting-network-technology-for-deck-handling-trials-of-x-47b-47220/
Rockwell Collins Tactical Targeting Network Technology (TTNT) was used by Northrop Grumman Corporation and the U.S. Navy as they successfully completed a series of deck handling trials of the X-47B Unmanned Combat Air System aboard the aircraft carrier USS Harry S. Truman (CVN-75). The exercises demonstrated the ability to maneuver the tailless, strike-fighter-sized aircraft quickly […]https://www.defencetalk.com/tactical-targeting-network-technology-for-deck-handling-trials-of-x-47b-47220/
Detailed geospatial map data provides Soldiers greater technology, in less time
Posted on
DefenceTalk The Sept. 11, 2012, attack on the U.S. Consulate in Benghazi, Libya reinforced the need for U.S. Army Africa to have at its fingertips the ability to draw upon the most up-to-date detailed maps and imagery of any given region at a moment’s notice. Project Manager Mission Command, or PM MC, is helping to streamline […]https://www.defencetalk.com/detailed-geospatial-map-data-provides-soldiers-greater-technology-in-less-time-46987/
The Sept. 11, 2012, attack on the U.S. Consulate in Benghazi, Libya reinforced the need for U.S. Army Africa to have at its fingertips the ability to draw upon the most up-to-date detailed maps and imagery of any given region at a moment’s notice. Project Manager Mission Command, or PM MC, is helping to streamline […]https://www.defencetalk.com/detailed-geospatial-map-data-provides-soldiers-greater-technology-in-less-time-46987/
China’s PLA controls hackers: US IT security firm
Posted on
DefenceTalk China’s army controls hundreds if not thousands of virulent and cutting-edge hackers, according to a report Tuesday by a US Internet security firm that traced a host of cyberattacks to an anonymous building in Shanghai. Mandiant said its hundreds of investigations showed that groups hacking into US newspapers, government agencies, and companies “are based primarily […]https://www.defencetalk.com/chinas-pla-controls-hackers-us-it-security-firm-46887/
China’s army controls hundreds if not thousands of virulent and cutting-edge hackers, according to a report Tuesday by a US Internet security firm that traced a host of cyberattacks to an anonymous building in Shanghai. Mandiant said its hundreds of investigations showed that groups hacking into US newspapers, government agencies, and companies “are based primarily […]https://www.defencetalk.com/chinas-pla-controls-hackers-us-it-security-firm-46887/
