Uncle Sam Wants YOU To Compete For Army Network Upgrade: CS 21
Posted on
Gone are the days of a stately, deliberate, laborious acquisition process in which the Army would plan out the future in detail before going to industry. “We’d almost always guess wrong,” said Maj. Gen. David Bassett. “Eventually we’d deliver yesterday’s technology tomorrow.”
Wearing The Network To War
Posted on
Army foot soldiers are going into battle with more and more electronics, wirelessly networked both to each other and to distant command posts. So can GI Joe be hacked?
Army Explores Robot Decoys & Cannon-Fired Jamming Pods
Posted on
Read entire article
Commerce Expands Huawei Black List Beyond US Shores
Posted on
Nicholas Eftimiades, a former senior US senior intelligence officer, said the Trump Administration policy “is very surgical in its approach,” and will have only a “moderate impact” on allied countries.
Big Data On The Army Front Line: DCGS-A Upgraded
Posted on
The Army is upgrading its intelligence system to give forward commanders full access to the cloud — and work when the enemy takes the network down.
Navy Wrestles With Cyber Policy As China and Iran Hack Away
Posted on
“We’re spending a lot of money in this area right now, but we don’t understand where we’re spending it” says Navy undersecretary Thomas Modly.
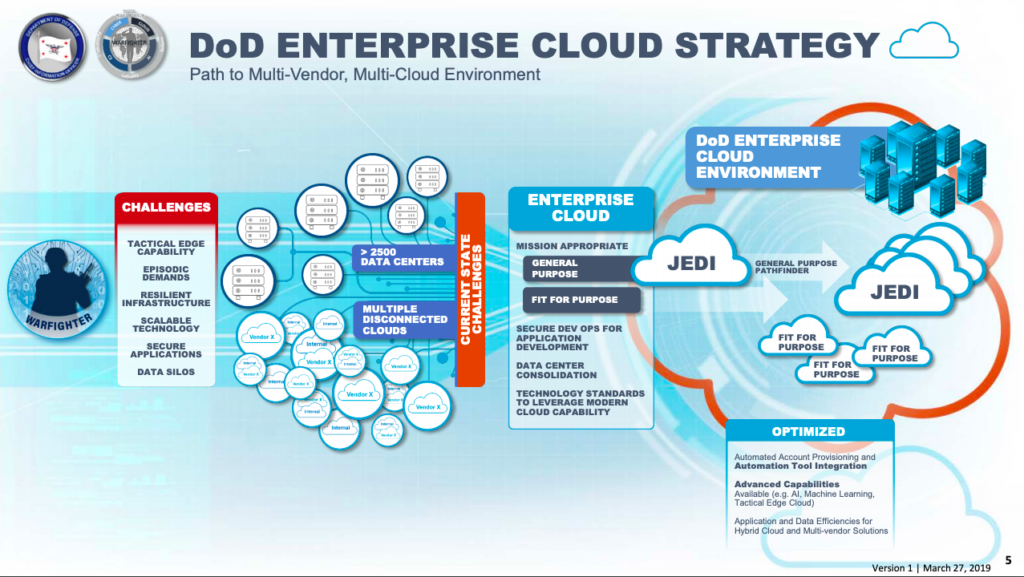
Download, Disconnect, Fire! Why Grunts Need JEDI Cloud
Posted on
Future soldiers will need to download huge amounts of intelligence data — then disconnect and go dark, like a submarine diving underwater to hunt its prey.
Big Data For Big Wars: JEDI vs. China & Russia
Posted on
Trump’s war with Bezos and Amazon has overshadowed the reason the military wants cloud computing: to share vital data in a fast-paced global conflict.
Mike Griffin Says 5G Top New Priority for R&E Shop
Posted on
“What I want to bet on is the ability of the United States and our Western allies to out-innovate adversaries,” says Mike Griffin, undersecretary of Defense for research and engineering.
A Secure Network Is Not Enough, Cyber Wargames Show
Posted on
If a hacker shuts off a base’s electricity or stops spare parts from arriving on time, they can sabotage a military mission without ever attacking a military network.